SSO Guide
A guide for Tuple customers who want to use SAML SSO to give their employees access to Tuple.
Specific SSO Setup Guides
General SSO Setup Guide
What you’ll need to enable a SAML configuration in Tuple:
- Your SSO IDP Entity ID
- Your SSO target url that performs authentication
- Your auth certificate or its SHA1 fingerprint
- Ensure your attributes include “first_name”, “last_name” and “email”
Tuple’s authentication URLs:
- Our entity ID: https://production.tuple.app/users/saml/metadata
- Our assertion consumer service (ACS) URL: https://production.tuple.app/users/saml/auth
Enabling the Configuration
Navigate to the Settings tab of the team management dashboard.
Note: Only Team Owners have access to this page, so you will need to be Team Owner to access this page. If you need to find out who the Team Owner for your team is, view your profile.
Toggle to Enable SAML, and the configuration form will be revealed:
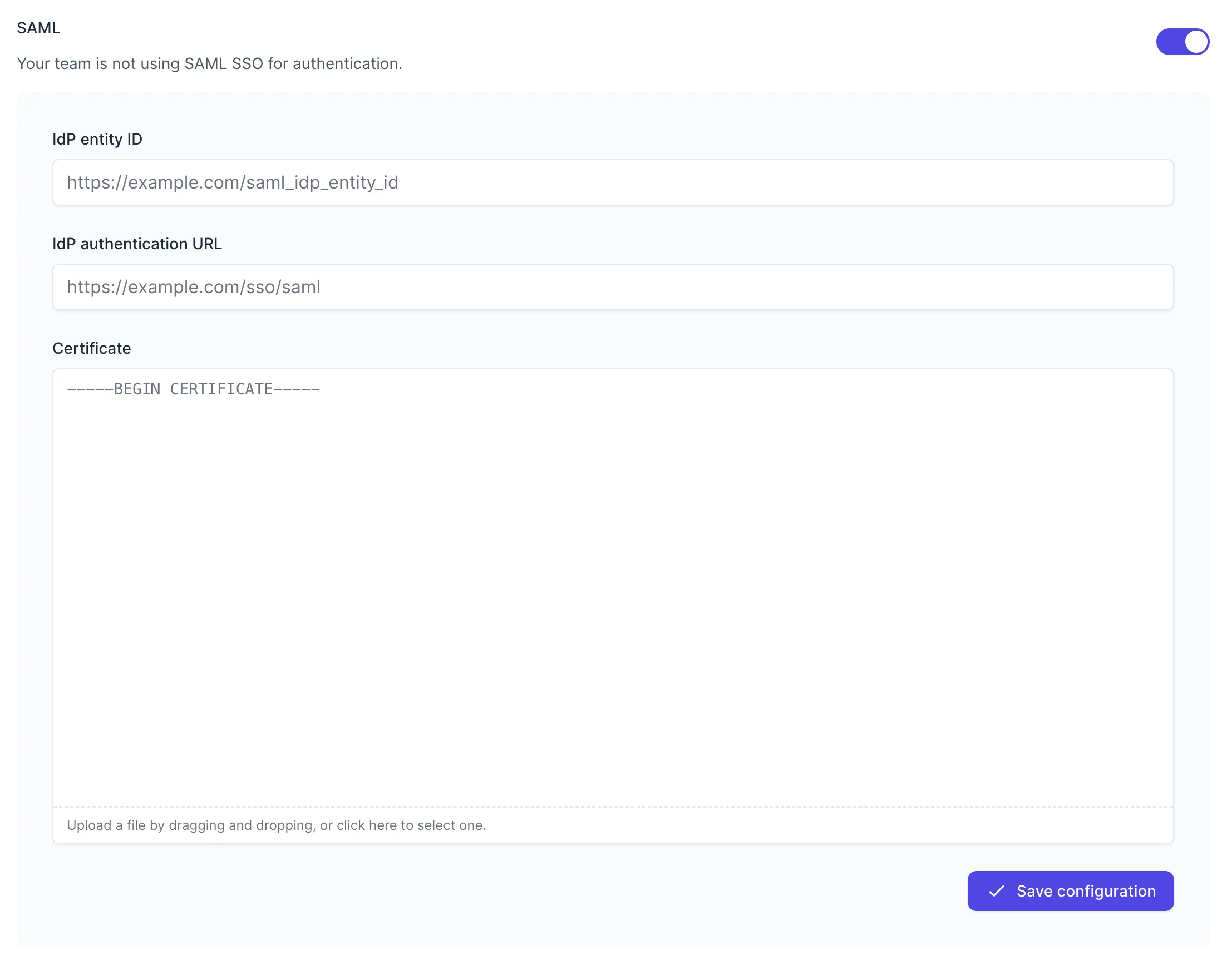
Fill in the values with your metadata:
- IdP entity ID - your
Issuer URL(Entity ID) - IdP authentication URL - your
SAML 2.0 Endpoint (HTTP)(authentication URL) - Certificate - the downloaded certificate file
Press “Save Configuration” to turn on SAML for your team. Once SAML is enabled, any active Tuple sessions will persist, but any new logins will be forced to authenticate using your provider. Log in here to verify that it’s working.
Provisioning/deprovisioning
The first time a new user authenticates to Tuple, we provision an account for them and (if you are on a per-seat billing plan) begin charging you for that seat. While you can disable a user’s access to Tuple in your IDP, deprovisioning the account such that you are no longer charged for it must be done in our team management page, accessible by your Team Owner.
Roles
We have only two roles in Tuple, Team Owner and User. By default, the Team Owner is the person who first created your team on Tuple, usually an engineering manager or developer. If you prefer to have an IT person be the team owner, just ask. Accounts provisioned via your IDP will be Users.
Permissions
Team Owners can add and remove users, invite unpaid guests, and update your billing information. Users can make and receive calls and add new Users.
Email Requirement
Email addresses for users in your SSO provider and on Tuple must match exactly. For example, dev+tuple@company.com will not match dev@company.com. Please ensure your team’s email addresses are correct before we enable the SSO integration.
Questions?
Please email us and we’ll get you straightened out.